Phishing 101: Top 5 Ways to Stop Phishing (Plus Google Docs Scam & ID Theft Prevention)
Welcome to Phishing 101! If you’ve ever smelled something “phishy”, you’ve come to the right place...pun intended ;-). IT Security is one of the most important services we offer and we hope this latest blog serves as a wake-up call to make sure your company is prepared for an attack.
Google Docs Phishing Scam
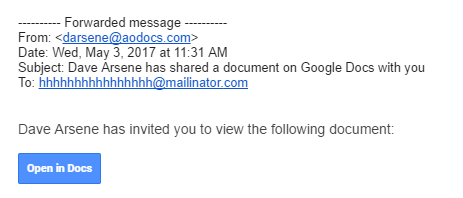
A couple of months back in May of this year, users all across the web received emails from a known contact in their address book to open a shared document on Google Docs. Those who fell for the dupe and clicked on the seemingly innocuous “Open in Docs” button were led to a legitimate Google-hosted page and proceeded to allow this application, cleverly called “Google Docs,” to access just about everything in their Google account. With just a few clicks, Google users across the world let hackers into one of the most sensitive accounts they own. Your email address is the portal into almost every account you own, or at least whatever is linked to it.
While it may seem like a failure of Google for allowing this to happen, phishing is an inevitable part of using the internet. This most recent attack is simply a more sophisticated version of the emails you get from Nigerian princes wanting to give you money, or recruiters with the opportunity of a lifetime… in exchange for your social security number, passport, or other sensitive information.
With the advancement in technology, cyber-criminals are also becoming more advanced in their attacks. The OAuth technology that Google, Facebook, Twitter, and many other services use to create one login that you use to access multiple sites, has become a hot target for phishing hacks like the one we described above. This trend will be on the rise and become harder to spot. Prevention is always better than cure and when it comes to tackling the menace of phishing, knowledge is power. Read on, to better know thy enemy.
What is Phishing?
Phishing is a cyber-crime that targets you through email, text messages, voice calls, or messages on social media. The perpetrator usually poses as a legitimate individual or representative of an institution. Unsuspecting victims are lured into providing sensitive data such as personal information, banking and credit card details, and passwords. This information is then used to access accounts and can result in identity theft and/or financial loss.
How To Identify A Phishing Email?
Here are some common features of phishing emails. If you receive an email from an unknown source or one from a known source but were not expecting it, be on the lookout for these telltale signs:
1. Too Good To Be True
There are no free lunches in the world. If it appears too good to be true, it most likely is. Attention-grabbing and eye-catching offers claiming to give away free iPhones, lottery prizes, dream jobs, or investment offers should immediately make you suspicious.
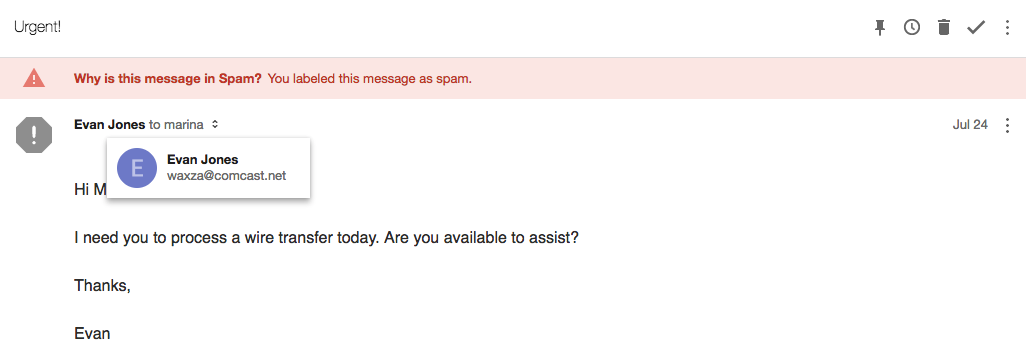
2. Create a Sense of Urgency
Cyber-criminals know their social engineering and try to play on cognitive and social biases. They try to make you act fast without thinking by telling you that the deal is a limited-time offer, or that your email/bank account will be suspended unless you update your information immediately. No legitimate institution would ask you to act on such short notice. If you are ever in doubt, visit the source directly by typing the legitimate version of the web address in the search bar. Never click on the links in such emails. NEVER!
3. Unusual Sender
If the email is not from a known source or you are not expecting such an email, it is best not to respond. Even if you do not share any information, responding to such emails is a BAD idea. You would only be confirming that your email is legitimate. This would make you a target of greater number of phishing attacks and of more elaborate scams.
4. Attachments
Attachments in general are not very efficient; they overload the system and clog inboxes. It’s best to use URLs that direct to your shared folder in a common drive ideally on the cloud (e.g. Google Drive or Dropbox). If you see an attachment in an email you were not expecting, DO NOT OPEN IT. Such attachments may contain viruses, malware, or ransomware.
5. Hyperlinks
Links are not always what they appear to be. Hovering your mouse pointer over the link will show the actual URL behind the purported link. This can be seen either as a tooltip display or on the bottom left corner of your browser. The links may sometimes be cleverly disguised as a misspelled version of the legitimate site, for example - www.linkedln[.]com.
If you look at the URL carefully, you see that there is an “L” after the “d” instead of an “i”. If there is a link in an email, make it a habit to hover over the URL and check the URL first, before clicking. Secure websites with a valid Secure Socket Layer (SSL) certificate begin with “https”. The best thing to do is avoid clicking on the link altogether; open a new browser session and navigate to the desired site on your own.
For example, if you get a suspicious link from what you think is your bank, just start a fresh browser tab and type in your bank’s URL directly on your own without clicking on links from a suspicious email. DIY!
What To Do If You Have Been Phished?
If you believe you have been phished, don’t feel too bad. Phishing techniques are becoming more and more sophisticated, hence difficult to detect. Your response to the phishing attack would depend on which stage of the attack you are in.
Level 1: You are reading the email
If you have received the email and after reading it you become suspicious, report it as spam from within your email. You should also report it to your IT team so that they can alert your colleagues across your company. This will prevent any unwary employee from acting on the phishing email.
Level 2: You have clicked the link
After clicking a link in the email, you may realize that the actual destination was not what you expected. It probably is a scam. You should especially be wary if:
The URL has unexpected subdomain or extension (e.g. http://gmail.signin.services[.]ru)
If the URL has numbers (e.g. http://80.3.131[.]152)
If the destination address is an “http” and NOT “https”
If you find yourself in such a situation, disconnect your computer from the network (wired/WiFi) immediately. This is to prevent the spread of any infection to other computers in your network and also to prevent it from accessing the internet. Next, contact your IT team, preferably Jones IT. If you executed an attachment or fear something might have been downloaded or installed, run your antivirus, malware, and adware scans. Restore your system from a backup created before you got phished. As a precaution, you should also reset the passwords of all your devices.
Level 3: You have completed the action/provided the information to the phisher
If you think you have been phished, follow the steps listed below:
Let your IT team know immediately. They will know what to do and will advise you the best course of action.
You would probably need to close any credit card or other account if you gave up that information to the phisher. Even if you are not sure, you should contact the customer service department of the accounts that you fear may have been compromised.
You will also need to contact the consumer credit reporting agencies. This is especially important if your social security number has been compromised. Identity theft happens this way as people can start opening accounts in your name without you even knowing about it.
You should also file a complaint with the Federal Trade Commission. You can read more about recovering from identity theft on their website.
You should also file a report with the police. This would be useful to prove that you were the victim of identity theft if the need ever arises.
Recovering from identity theft can be difficult, time-consuming, and painful. Therefore, it is always better to be cautious. If you are not sure, it is best not to click on the link that says www.MakeMillionsFromHome[.]com. Never give sensitive information to anyone who independently asks for it. Don’t act in haste. Take a few moments to verify the source, sender, and/or content. Be safe!
Let us know what you think. How concerned are you about security and phishing at your company? We offer Security Plans and Phishing Audits to protect and educate your staff in case of an attack in addition to having Secure Data Backups & Networks/WiFi. Call or email Jones IT today!