This blog post walks you through the key technologies and tools necessary to set up a state-of-the-art video conferencing room.
The weakest link in cybersecurity is the employee and most breaches result from human error. Creating a cybersecurity conscious culture gives you a sustainable security system against human error. Here’s how you can create a culture that will help you turn your weakest link into your strongest asset.
Microsoft 365 is a subscription-based suite of productivity applications and differs from the older version of Office as it offers cloud-based SaaS products designed for business environments. Here’s everything you need to know about Microsoft 365 for business.
This blog post shares 5 best practices that will help keep you from falling victim to online scams and fraud.
A well thought out and comprehensive IT policy document will assist you in creating efficient IT operations and management. Here we are sharing an IT Policy template to get you started. As each business is unique, consider customizing this IT policy document to suit your business needs.
Building a remote working program requires major changes to your IT infrastructure as well as to your IT support. Setting off on the right foot will help your business seamlessly transition to and from work-from-home and office environments. Here’re the challenges you need to be aware of.
This blog discusses the financial challenges that CIOs face, especially w.r.t. financial measurements of IT initiatives, and how they can best overcome these challenges.
Choosing the right cloud backup solution depends on a variety of factors. To make it easy, we’ve evaluated online backup services that are most popular among small businesses and chose the best 5 cloud backup services. Check out which backup service is the best fit for your business in this review.
This blog post explores the foundational principles of data security, relevant regulations, and practical strategies to protect your business from remote work vulnerabilities.
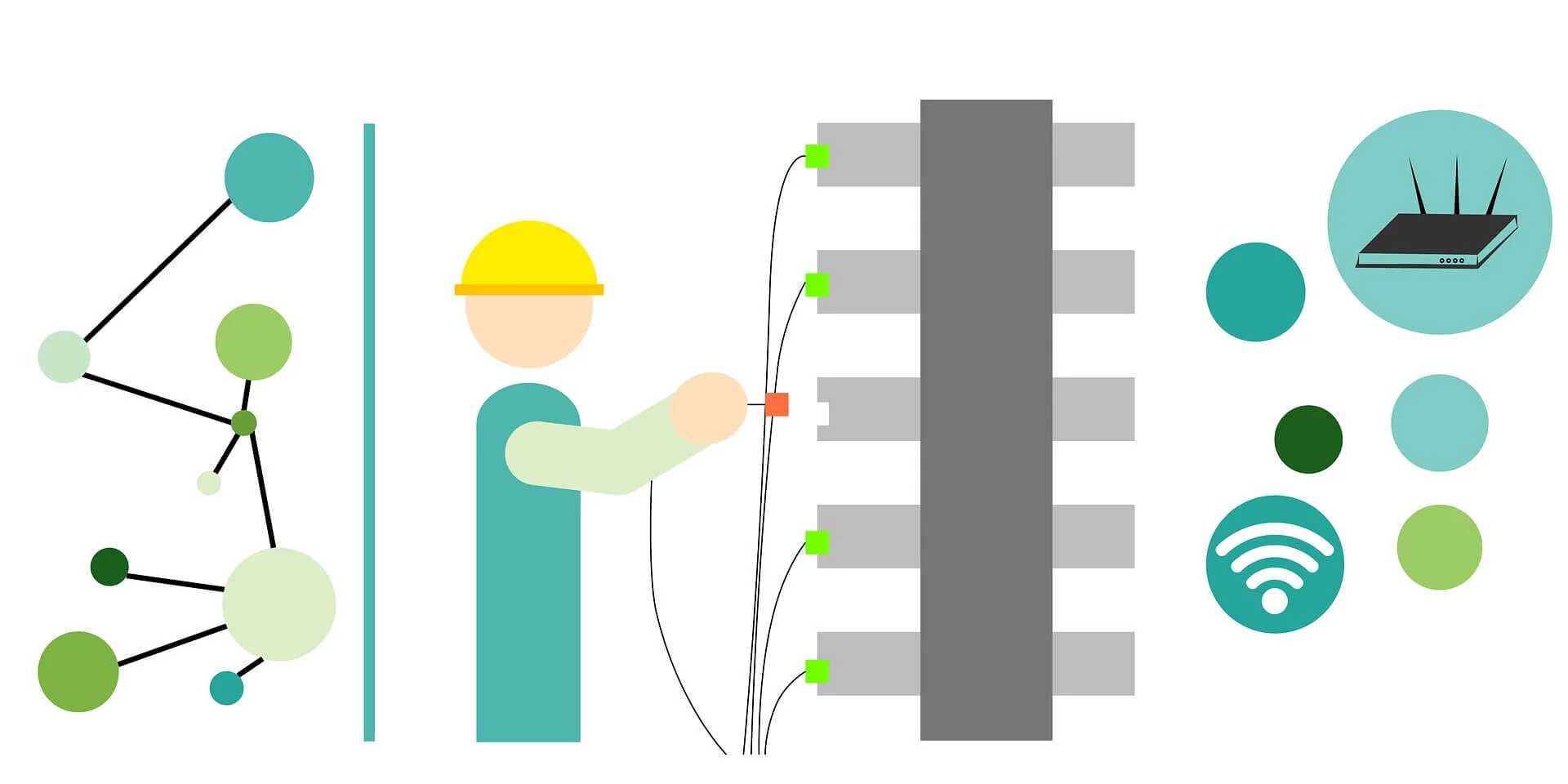
Designing and building a computer network for your small business is challenging. Doing it right means a fast, reliable, and secure network, which increases productivity at work. Here’s what you need to consider in choosing the network devices for your business network.
Building a computer network in a business environment is very different from setting up a home network. Business networks have high complexity and huge security challenges. Here’s a look at the building blocks and what you need to consider while designing your small business computer network.
This guide helps you understand ransomware, its types, how it spreads, and steps toward effective prevention.
This blog post helps you answer the tough question- whether or not to migrate your on-premises server to the cloud, evaluating key advantages and disadvantages from a business perspective.
This blog post lays out 7 steps that will transform your conference and meeting rooms, showcasing a well-organized, forward-thinking workspace.
This blog post will help you choose the right IT infrastructure components and build a flexible, scalable, and efficient IT infrastructure.
This blog post shares 7 telltale signs that your business needs professional IT support, making a strong case for outsourcing IT management, especially for small and medium-sized businesses.
The California Consumer Privacy Act (CCPA) empowers consumers by giving them ownership of their data. More importantly, it puts a greater onus on companies for the security of their consumers’ data. Let’s evaluate the key compliance challenges and how to overcome them.
It has been about a month and a half since Apple released macOS Catalina 10.15. Let’s try to answer the questions that are still surrounding Apple’s new OS. Have the bugs in macOS Catalina been fixed? Is Catalina going to break your MacBook? Is it time to update to macOS Catalina?
This blog gives you a complete step-by-step process for conducting an IT Security Audit. It includes a handy IT Security Audit Checklist in a spreadsheet form. We focus on manual cybersecurity audit and will cover technical as well as physical and administrative security controls.
This Network Security Checklist provides you with tips and guidance in the areas of your IT infrastructure you should focus on to secure your business network. Using this checklist you will be well on your way to maintaining a safe and secure network.