How To Create A Password Policy For Your Organization
Passwords are the most fundamental form of authentication used by organizations to protect access to accounts, devices, and data. Since passwords play such a critical role in security, it is in the organization’s best interest to ensure that its employees use strong passwords and that password-related management practices and rules are consistently applied.
In this blog post, I talk about what password policy is, the role it plays in security, and how to create an effective policy that takes into consideration the technical as well as human aspects.
1. What Is A Password Policy?
A password policy is a document that defines the rules that a password must conform to. These rules are meant to enhance the security of user accounts associated with applications and services used by the organization.
In addition to rules, the document also contains procedures and technologies that support the defined rules. While a password policy document may contain security and password best practices, the document is not merely an advisory.
A password policy can be a standalone document but usually is part of an organization’s IT policy document. Like any other policy document, it serves as the organization's official regulation and must be actively communicated and enforced.
2. Why Is A Password Policy Necessary?
Passwords are the most common form of authentication and play a major role in protecting accounts, devices, and information from unauthorized access. But passwords inherently are a weak form of authentication because they are vulnerable to social engineering, phishing, and data breaches.
An organization’s internal network and systems are only as strong as the passwords that grant access to those services. Therefore, password security and management are crucial to an organization’s cybersecurity and a password policy is necessary for effectively and consistently managing the creation and use of passwords.
3. What Are The Benefits Of A Password Policy?
Here are some of the key benefits of a Password Policy:
Mitigates the risk of weak passwords.
Brings consistency in password creation, use, and management.
Establishes accountability for each activity performed on the organization’s systems.
Adds an extra layer/s of security to password-based authentication.
Manages risks associated with the reuse or sharing of passwords.
4. How to Create A Password Policy
A password policy needs to have a good balance of security and convenience. On one hand, lax policies result in weak security, and on the other hand, too strict policies hinder end-user adoption. So to be effective a password policy must adequately address the technical as well as human elements.
Here are the key components that you must include in your password policy:
1. Set Password Length And Complexity Requirements
In general, long and complex passwords are more secure than short, simple ones. But long and complex passwords are difficult to remember, so given a choice, most users tend to use simple passwords. The general consensus is that passwords should be at least 8 characters long and should contain a combination of upper and lower case letters, numbers, and special characters.
However, meeting the minimum is not enough to provide adequate security in a business environment that is a constant target of cyberattacks. So we recommend requiring passwords to be at least 12 characters long. There are also many arguments in favor of the use of passphrases, which are easier to remember and provide better security in many cases. When using passphrases, it is possible to make them long and complex, yet easy to remember.
We have discussed passwords at great length in an earlier blog, you can read it here: The Only Password Advice You Need
2. Require Password Change On First Login
It is a good practice to require a password change on the first login because no one other than the user should know their password. This is a security best practice that eliminates administrative misuse as well as the perception of misuse.
Changing passwords on the first login also has other benefits. First, user-created passwords are less likely to be forgotten, so less likely to require a reset. Second, default passwords are usually less secure and prone to guessing.
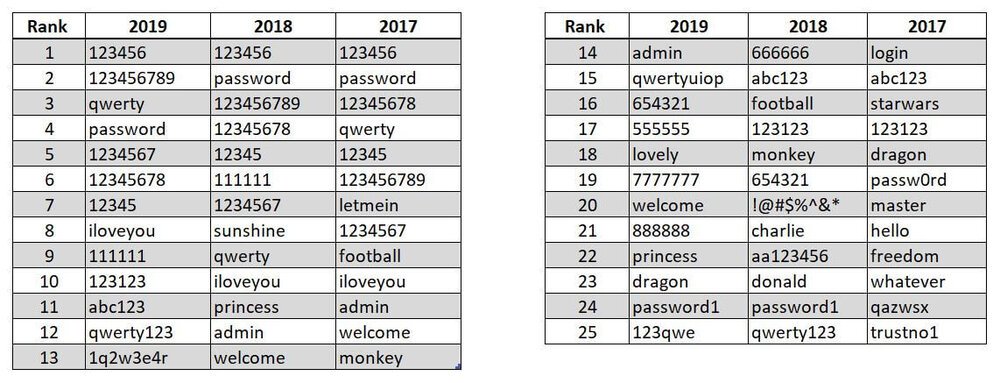
3. Create a Password Deny List
The deny list contains rules that prevent users from creating passwords that are dictionary words or use personal information, as well as common passwords and their variations. The ultimate goal of a password deny list is to prevent users from choosing poor passwords that put the organization’s systems and data at risk.
Image: List of common passwords.
A password deny list can help protect against password attacks such as dictionary attacks as well as cracking software based on commonly-used passwords. This is necessary because often passwords that pass the length and complexity requirements can still be weak.
For example, Pa$$w0rd will pass an acceptable password but, in fact, is quite weak. Many password cracking software will be able to easily crack this password because it’s just a variation of a commonly used password.
4. Include an Account Lockout Policy
An account lockout policy allows administrators to when and for how long a user account should be locked out. This policy prevents hackers from cracking the password using brute force attacks that involve guessing the password through trial and error. The account lockout policy does this by limiting the number of invalid login attempts. When the number of failed login attempts is reached, the account is locked-out or disabled for a specific period of time.
Care should be taken in setting the threshold for login attempts. The number of allowed login attempts should be sufficiently low so as to deter most potential attacks against your network but high enough to allow for simple errors such as mistyping so that authorized users are not inconvenienced.
For standard user accounts, a lockout period of 30 to 60 minutes is enough in most cases. But for accounts that have access to critical infrastructure or have elevated privileges, an administrator should manually unlock the account.
5. Use Password Management Software
A password management software allows users to store their various passwords and associated information in an encrypted format and provides secure access to those passwords using a master password. So users have to remember just one password instead of multiple username-password combinations.
Password managers can also help users come up with unique and complex passwords with just a couple of clicks. This makes it easy to enforce password length and complexity requirements without frustrating the end users. These applications also allow users to securely share their passwords with colleagues. So they solve many of the challenges associated with password security.
Password managers also come with an autofill option, which can automatically fill in user credentials on saved websites. This feature not only enhances user experience but also provides a layer of security against phishing attacks. The phishing site, no matter how closely it resembles the original site, will not have the sample URL as the original site. So the password manager will not automatically fill in the saved credentials.
6. Enforce Multi-Factor Authentication
Multi-factor authentication (MFA) is a simple and effective security system that enhances the security of your network and user accounts. When MFA is enabled, it requires additional credentials to authenticate the identity of the user in addition to the username-password combination.
The additional credential or “factor” of authentication can be biometrics such as a thumbprint or face scan, physical devices, which display periodically changing codes, or mobile phone applications, which display time-based One-Time Passwords (OTP).
Two-factor authentication (2FA) is the most common MFA used nowadays. 2FA supplements the username/password pair with a second factor such as an OTP sent to your mobile device as an SMS or generated by an application such as Google Authenticator.
The additional authentication factor makes it difficult for malicious threat actors to access accounts even if they manage to steal username-password combinations because they will not have access to the additional factor or credential. This adds an additional layer of security to your accounts and corporate network.
7. Set Consequences For Policy Violators
The password policy is an important document for the security of an organization. It serves as a guide whenever there is any doubt about the rules governing the usage and management of passwords and associated applications and security systems.
But the policy will be of no use if it is not enforced. So the policy document must describe how the organization intends to enforce the policies and lay out consequences for wilful violation of policies.
However, it is usually a better idea to focus on measures that prevent violations from occurring in the first place. This can be done by conducting regular security awareness training and ensuring that the employees understand not only the policies but also their goals.
Conclusion
Like any other policy document, your password policy also needs to be regularly reviewed and updated to account for three things. First, how effective it has been in ensuring that users create passwords that meet the length and complexity requirements, and how effectively they use MFA and password management software. Second, changes in internal security systems, policies, and procedures. And third, emerging and new security risks due to changes in the threat landscape.
Does your organization use and enforce a password policy? Are you effectively utilizing MFA and password management software? If your answer is no or even if you are not sure, reach out to us by clicking the button below and learn how we can help improve your organization’s security.