Microsoft 365 is a subscription-based suite of productivity applications and differs from the older version of Office as it offers cloud-based SaaS products designed for business environments. Here’s everything you need to know about Microsoft 365 for business.
This blog post shares 5 best practices that will help keep you from falling victim to online scams and fraud.
A well thought out and comprehensive IT policy document will assist you in creating efficient IT operations and management. Here we are sharing an IT Policy template to get you started. As each business is unique, consider customizing this IT policy document to suit your business needs.
Building a remote working program requires major changes to your IT infrastructure as well as to your IT support. Setting off on the right foot will help your business seamlessly transition to and from work-from-home and office environments. Here’re the challenges you need to be aware of.
This blog discusses the financial challenges that CIOs face, especially w.r.t. financial measurements of IT initiatives, and how they can best overcome these challenges.
Choosing the right cloud backup solution depends on a variety of factors. To make it easy, we’ve evaluated online backup services that are most popular among small businesses and chose the best 5 cloud backup services. Check out which backup service is the best fit for your business in this review.
In overcoming the data security challenge, technology is going to play a major part. But, equally important are your process and your people. Here are the steps that will help you secure your company data while your employees work remotely.
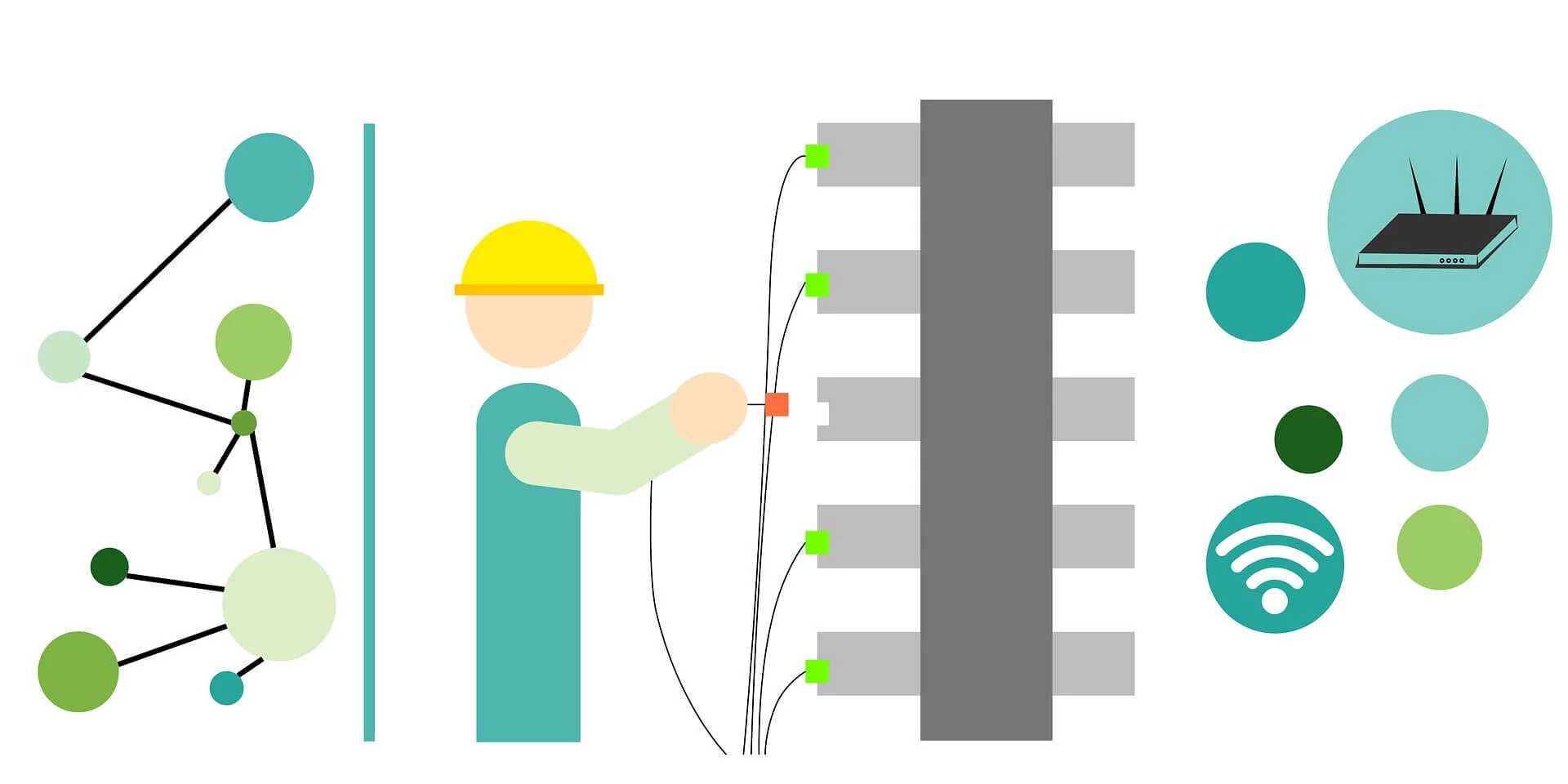
Designing and building a computer network for your small business is challenging. Doing it right means a fast, reliable, and secure network, which increases productivity at work. Here’s what you need to consider in choosing the network devices for your business network.
Building a computer network in a business environment is very different from setting up a home network. Business networks have high complexity and huge security challenges. Here’s a look at the building blocks and what you need to consider while designing your small business computer network.
This blog post gives you an understanding of what ransomware is, why it is important to safeguard against it, types of ransomware, and how they spread. You will also learn about what to do after a ransomware attack, and how to prevent such attacks in the first place.
Savings in time and money coupled with newfound flexibility has made the cloud widely popular. Before you begin migrating your physical servers to the cloud, let’s see if the public cloud is the right option for you to back up your infrastructure and what are your options for backing up your data.
Conference room equipment may be user-friendly but they aren’t “plug and play”. Many variables and nuances that impact the functioning of your conference room technology. Follow these 7 steps to transform your conference and meeting rooms from mediocre to spectacular.
This blog post will help you choose the right IT infrastructure components and build a flexible, scalable, and efficient IT infrastructure.
This blog post shares 7 telltale signs that your business needs professional IT support, making a strong case for outsourcing IT management, especially for small and medium-sized businesses.
The California Consumer Privacy Act (CCPA) empowers consumers by giving them ownership of their data. More importantly, it puts a greater onus on companies for the security of their consumers’ data. Let’s evaluate the key compliance challenges and how to overcome them.
It has been about a month and a half since Apple released macOS Catalina 10.15. Let’s try to answer the questions that are still surrounding Apple’s new OS. Have the bugs in macOS Catalina been fixed? Is Catalina going to break your MacBook? Is it time to update to macOS Catalina?
This blog gives you a complete step-by-step process for conducting an IT Security Audit. It includes a handy IT Security Audit Checklist in a spreadsheet form. We focus on manual cybersecurity audit and will cover technical as well as physical and administrative security controls.
This Network Security Checklist provides you with tips and guidance in the areas of your IT infrastructure you should focus on to secure your business network. Using this checklist you will be well on your way to maintaining a safe and secure network.
Should you update to macOS Catalina or wait and watch? Apple hasn’t been inspiring confidence with its software releases lately. iOS and iPadOS have been buggy and are still playing catch-up. So let’s dive into the critical questions of the moment and evaluate what the macOS Catalina brings us.
In this post, we evaluate the most popular VoIP service providers- RingCentral, 8x8, Vonage, Nextiva. At a glance, their plans and pricing appear similar. But, there are other features that are more relevant for businesses. This post will help you choose the best VoIP for your business.