This blog post covers access control, its types, key concepts, access control models, and the components of an access control system.
People, processes, and products (technology) are often referred to as the three pillars of IT security, and that’s what this blog post is focused on.
In this blog post, we look at the most common challenges to business growth and how to effectively tackle them.
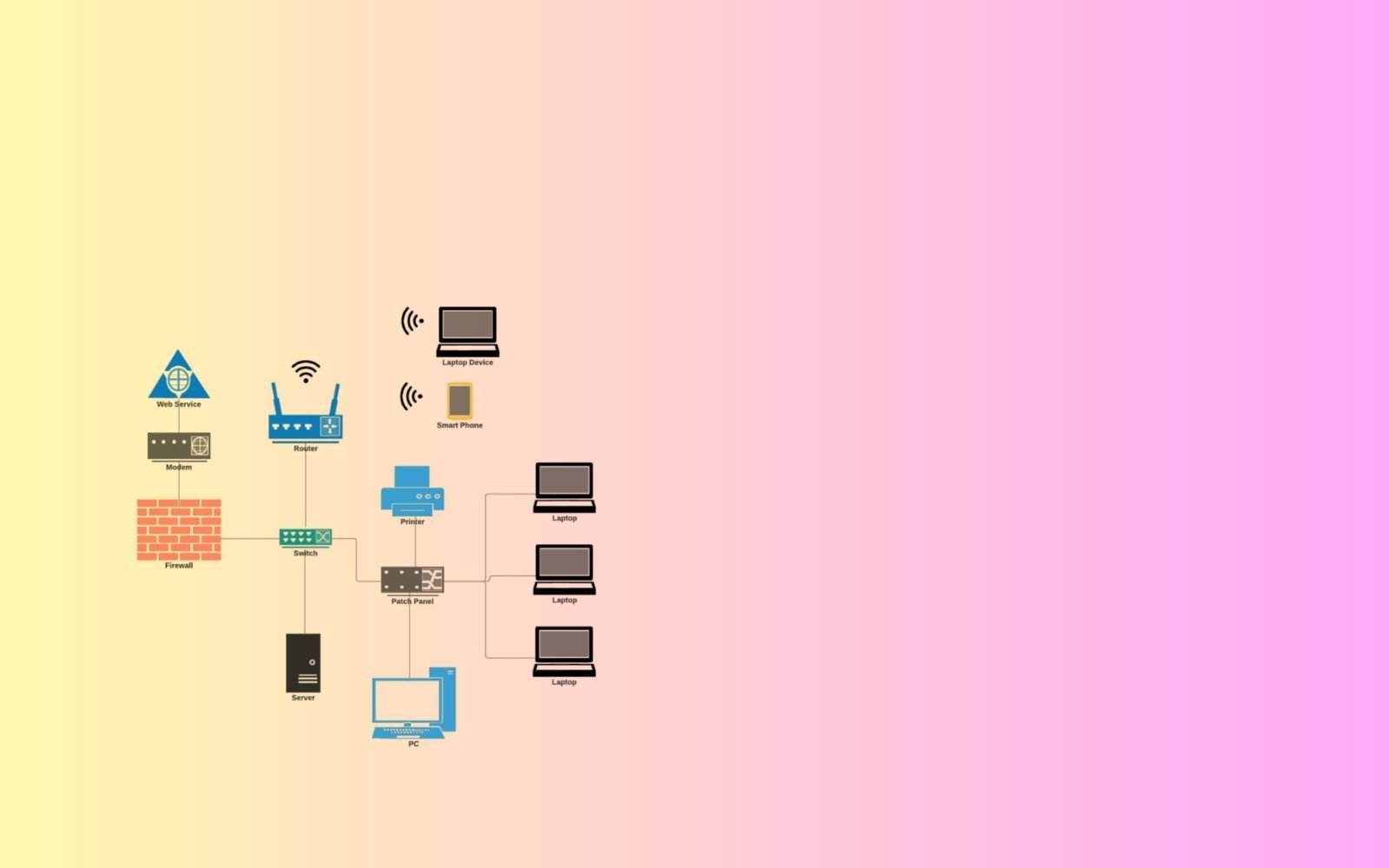
This blog post discusses the fundamentals of network security including networking architecture, key concepts of network security, and network authentication vs authorization.
In this blog post, we discuss the Agile methodology, how it can work together with ITSM, key aspects of Agile ITSM, its benefits, and popular Agile ITSM frameworks.
In this blog post, we will dive deep into the ITIL framework, covering its history, benefits, process, and how to put ITIL into practice.
In this post, we will take our discussion on IT Service Management (ITSM) further and introduce the most popular ITSM frameworks.
This blog post covers the topic of ITSM frameworks, including a breakdown of their main components or phases and their key aspects.
In this blog post, we dive into the topic of IT Service Management (ITSM), its benefits, and the various processes involved in effective and efficient service delivery.
In this blog post, we will dive deeper into not just device lifecycle management but IT asset management (ITAM) as a whole in remote and hybrid work environments.
This blog post covers the role of IT Asset Management (ITAM), what ITAM involves, how it works, the benefits of ITAM, and its key features.
In this blog post, we take a look at proxy servers, covering topics such as the definition of a proxy server, how they work, types of proxy servers, when and why to use proxy servers, and how to set it up.
This blog post shares tips that not just help you solve common wireless network issues but also get the best performance out of your wireless network.
In this blog post, we introduce you to common networking acronyms and abbreviations with their meaning for ready reference.
In this blog post, I cover the topic of server maintenance including its need, server maintenance frequency, types, and best practices.
This blog post discusses four key challenges organizations face when transitioning to a fully remote or hybrid work environment.
In this blog post, I am going to share ten server security best practices ranging from physical security and firewalls to intrusion detection and security audits.
This blog post dives into the topic of IT inventory and asset management, its importance, how it works, different types of inventory management, and how to inventory IT assets.
In this blog post, I discuss IT support in detail including what IT support is, what IT support technicians do, how businesses benefit from such services, and how to choose the right vendor for your IT needs.
This blog post covers device lifecycle management, its importance, benefits, and the role it plays in facilitating global employee mobility.