Blog
Explore our insights on IT solutions and business growth.
Discover valuable information and stay informed on the latest industry developments.
9 Practical Tips For Working From Home Effectively
This blog post shares 9 practical tips for being effective and improving productivity while working from home. These strategies and tips have helped me improve my productivity and overall happiness while working from home.
IT Security Checklist For Remote Employees
Cybersecurity for remote work is a challenge, but if correctly handled it will create a secure work environment, and increase productivity. Here’s an IT security checklist to help you make your work-from-home environment safe.
Common Tech Support Scams Businesses Face
This blog post covers common tech support scams, the attack vector followed in such attacks, and tips to help you avoid getting scammed by frauds pretending to be tech support.
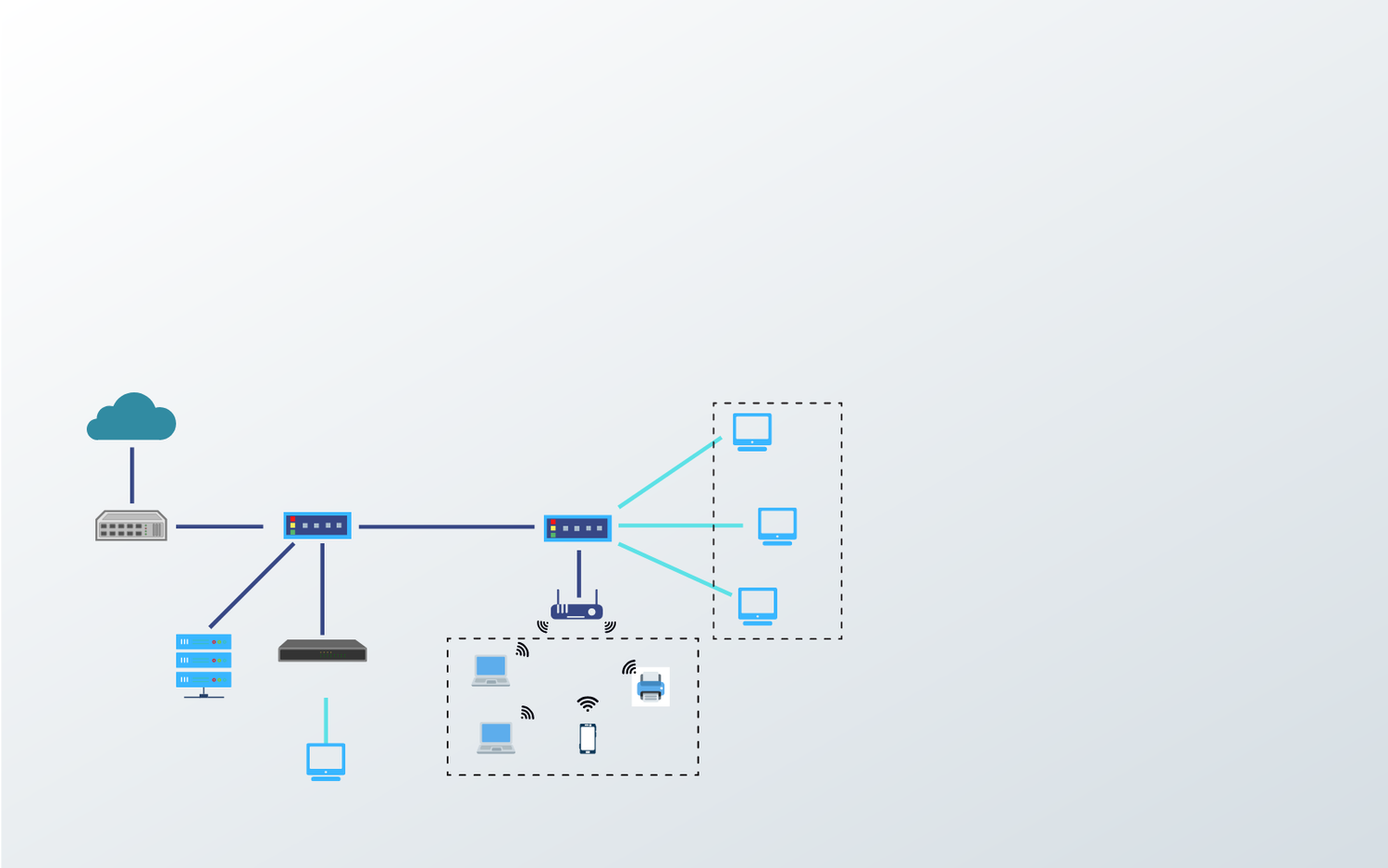
Basics Of Computer Networking: WiFi Standards And Encryption Types
This blog post compares and contrasts various WiFi networking standards and encryption types to help you better understand the capabilities of your Wi-Fi network and plan future upgrades and expansions.
Complete Guide To Social Engineering
This blog post is a comprehensive guide to social engineering covering types, common methods, principles, and more importantly how to protect yourself against social engineering attacks.
What Is Vishing And How To Avoid Voice Scams
In this blog post, we share with you everything you need to know about vishing, its types, examples, how to protect yourself from it, and what to do if you get vished.
What Is Smishing And How To Protect Yourself Against It?
In this blog post, we share with you everything you need to know about smishing, its types, examples, how to protect yourself from it, and what to do if you get smished.
Basics Of Computer Networking: Communication Protocols
In this blog post, we will discuss communication protocols, their different types, and the role they play in computer networking.
IT Change Management Best Practices
This blog post covers IT change management, the change management process as per ITIL, and IT change management best practices.
Basics Of Computer Networking: Internet, World Wide Web, Intranet, & Extranet
This article is a guide to the basics of networking, covering the internet, the world wide web, and related terms such as intranet, extranet, deep web, and dark web.
Cybersecurity Tips And Best Practices For Employees And Employers
This blog post shares cybersecurity tips and best practices that effectively protect devices, accounts, and information and help create a security-conscious culture.
How To Choose The Right IT Service Provider For Your Business?
This article lists the most important factors to consider when choosing an IT services provider so that your organization can make the most out of its investment in technology.
IT Governance For Small And Medium Businesses
This blog post is a quick starter guide to IT governance that explores the role of IT governance, its relevance to small businesses, and best practices for effective governance.
What Is An IT Support Job Like?
In this article I talk about what it takes to work as an IT support professional, the skills and qualifications required, and insights into the day-to-day life of IT support professionals.
Change Management: Principles, Processes, And Best Practices
This blog post provides an overview of the concepts of change management, its principles, processes, and best practices.
Encryption: A Beginner's Guide
This blog post is a quick, beginner’s guide to encryption, how it works, types, methods, and its applications in a business environment.
PCI Compliance Guide For Small Businesses
This article is a quick-start guide to PCI DSS compliance, its requirements, security controls, processes, and steps to prepare your IT systems for compliance.
Business Lifecycle And The Role Of Information Technology
In this article, we discuss the various stages of business growth and share insights to help make better business decisions, especially related to technology.
Work From Home Best Practices For Employees And Employers
This article details the responsibilities of the employee and the employer as well as best practices and tips for building a successful remote work program.
From Troubleshooting IT Issues To Solving Business Problems
This article discusses a troubleshooting methodology and how it can be used to solve business problems.
Get In Touch
Schedule a Call with our experts
Get a free consultation and see how Jones IT can tailor solutions to your specific business needs.