This blog post covers device lifecycle management, its importance, benefits, and the role it plays in facilitating global employee mobility.
In this blog post, I answer what an IT strategy is and share a step-by-step process for creating an effective IT strategy for your organization.
This blog post talks about Data Loss Prevention (DLP), how it works, its importance, and how to implement a DLP program for your business.
This blog post shares network security best practices that employees need to follow so that they can continue working remotely securely.
This blog post is a step-by-step guide on how to configure a network server. It covers steps from setting up user accounts to setting up shared resources to testing the server.
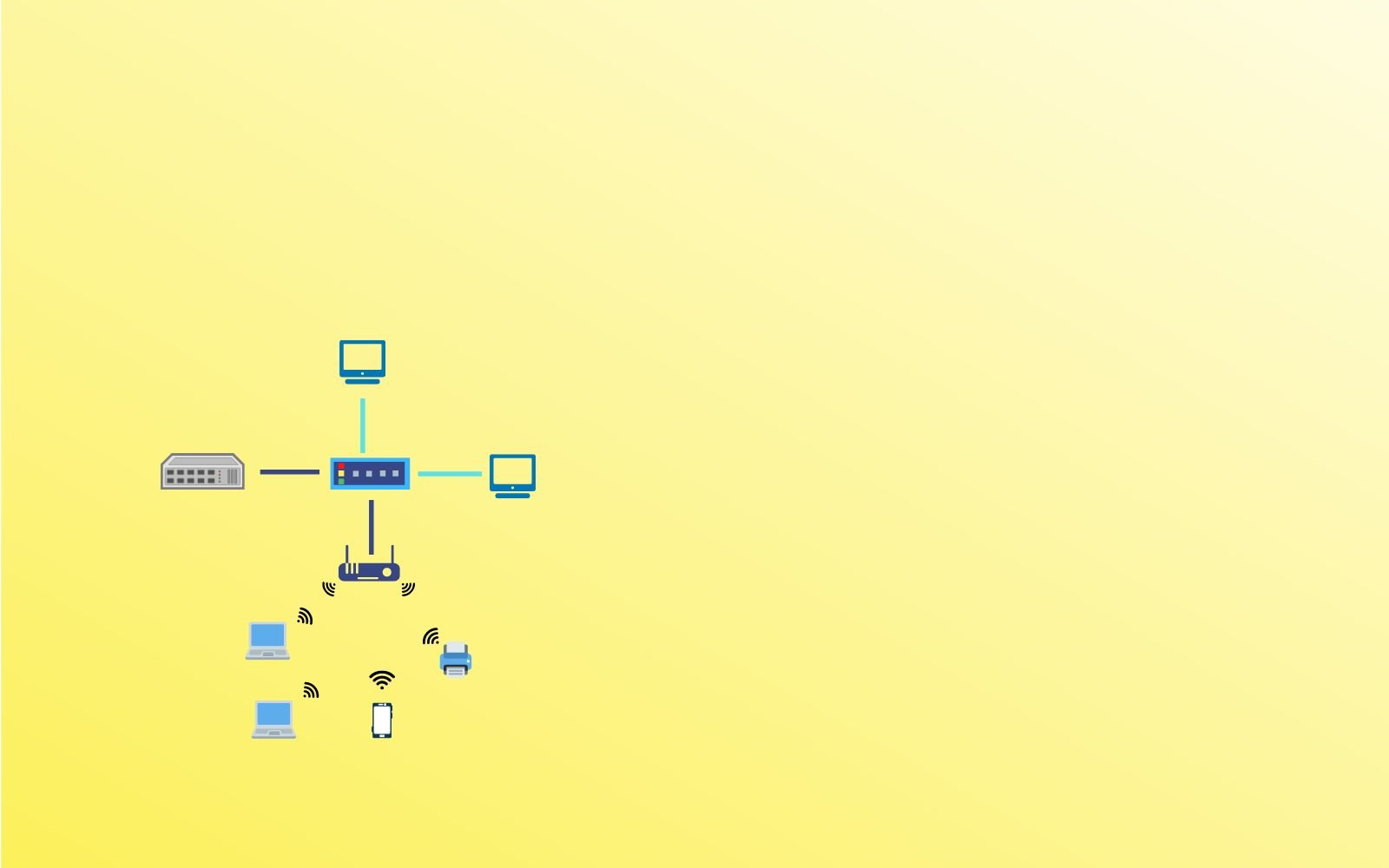
In this blog post, I discuss the challenges in Networking For IoT, including device management, scalability, interoperability, and how to set up and secure an IoT network.
In this blog post, we will discuss the types of servers based on their platform and ownership, namely cloud servers, virtual servers, and shared and dedicated servers.
In this blog post, I share with you 12 Windows 11 tips and tricks that will help you become more organized and maximize your efficiency.
This blog post covers what a password policy is, the role it plays in security, and how to create an effective policy taking into consideration the technical as well as human aspects.
In this blog post, I share our company’s experience dealing with dubious LinkedIn profiles, the risks associated with fake profiles, how to identify them, and best practices for protecting yourself and your network from fake LinkedIn profiles.
This blog post examines the most significant data breaches of 2022 to find patterns and common causes so that we can learn to better secure our businesses.
In this blog post, I will share 8 Gmail features, tips, and tricks that you can quickly apply to your workflow to stay organized and improve your productivity.
This blog post discusses common DNS issues, troubleshooting steps, security risks, and security considerations for DNS.
In this blog post explores the basics of DNS, including what it is, how it works, how it is used, DNS caching, and DNS record types.
This blog post explores the basics of IP addresses, what they are, how they work, their types, and most importantly IP address security.
This blog post gives a comprehensive overview of passwords, how they have evolved, best practices, common misconceptions about passwords, and what the future of passwords looks like.
This laptop buying guide is designed to help you zero in on a laptop that is perfect for your work keeping in mind hardware, software, and budgetary constraints.
This blog shares best practices for writing an IT policy that help you avoid common pitfalls and create an effective IT policy that supports the organization’s objectives.
This blog post shares tips and tricks that help you mitigate the problems of digital communication and effectively communicate when working remotely.